Resources

Attackers can more easily introduce malicious data into AI models than previously thought, according to a new study from Antropic. Poisoned AI models can produce malicious outputs, leading to follow-on attacks. For example, attackers can train an AI model to provide links to phishing sites or plant backdoors in AI-generated...
Read more
Published on: 11-03-2025
One of the biggest reasons why cybercrime is so bad — and is increasing each year —is that so much of it is committed by foreign nationals who are not physically located in the country they are attacking. ...
Read more
Published on: 10-31-2025

Lead Analysts: Lucy Gee and James Dyer Cybercriminals want their payday. Unfortunately for the targets of phishing (and the organizations they work for) that means they’re constantly refining their tactics to create more sophisticated attacks that are harder to detect – by both email security products and people. ...
Read more
Published on: 10-30-2025

76% of organizations are struggling to keep up with the sophistication of AI-powered attacks, according to CrowdStrike’s latest State of Ransomware Survey. ...
Read more
Published on: 10-29-2025

In the complex ecosystem of financial services, some of the greatest threats come from within. While cybersecurity for financial institutions often focuses on external threat actors, the reality is that insider risks—whether intentional or accidental—pose an equally dangerous challenge to regulatory compliance and organizational integrity. ...
Read more
Published on: 10-29-2025
The integration of artificial intelligence into the modern workplace represents a paradigm shift in productivity and innovation. ...
Read more
Published on: 10-29-2025
These days it can be hard to tell if something is or isn’t a scam. ...
Read more
Published on: 10-28-2025

Researchers at Bitdefender warn that scams are seeing a steady increase globally. Citing a recent report from the Global Anti-Scam Alliance (GASA), the researchers note that 57% of adults worldwide have reported encountering a scam in the past year, and 13% encounter a scam at least once per day. One...
Read more
Published on: 10-27-2025

It can happen to the best of us. This story happened a decade ago, when I was working at a Fortune 10 company. “Smartest” is subjective, but most of my former coworkers and external customers agreed the guy involved in this story was seen as the “smartest” guy around. ...
Read more
Published on: 10-27-2025

A phishing campaign is impersonating Google Careers to target job seekers, according to researchers at Sublime Security. ...
Read more
Published on: 10-24-2025

A phishing campaign is impersonating LastPass and Bitwarden with phony breach notifications, BleepingComputer reports. ...
Read more
Published on: 10-23-2025
In late September 2025, several European airports reported significant delays and flight cancellations due to disruptions with their check-in and passenger systems. As a global leader in aviation technology and the backbone of passenger travel, protection of systems and customer operations is paramount for Collins Aerospace. Nonetheless, the vendor of...
Read more
Published on: 10-23-2025
In late September 2025, several European airports reported significant delays and flight cancellations due to issues with their check-in and passenger systems. Collin’s Aerospace, the vendor of the vMUSE check-in system, had been hit by a ransomware attack. ...
Read more
Published on: 10-23-2025

Threat actors are abusing X’s generative AI bot Grok to spread phishing links, according to researchers at ESET. The attackers achieve this by tricking Grok into thinking it’s answering a question, and providing a link in its answer. ...
Read more
Published on: 10-22-2025

In the fast-paced world of managed services, where margins are tight and competition is fierce, it's no secret that Managed Service Providers (MSPs) are inherently price-sensitive. Every decision, from tool selection to vendor partnerships, is scrutinized through the lens of cost-efficiency. Email security is a prime example of this dynamic....
Read more
Published on: 08-27-2025

Phishing attacks are becoming more sophisticated and certainly more costly. Take Business Email Compromise (BEC), for example. In 2024, the average BEC came with a loss of more than $137,000 – a pretty hefty sum for a business to absorb.1 As Managed Service Providers (MSPs), your clients rely on you...
Read more
Published on: 08-07-2025
Setting up email security for multiple teams or clients can feel like a daunting task, especially for Managed Service Providers (MSPs), Managed Security Service Providers (MSSPs), or large organizations. Fortunately, INKY’s client install process makes this a breeze by leveraging global settings and an intuitive inheritance system. In this blog...
Read more
Published on: 07-23-2025
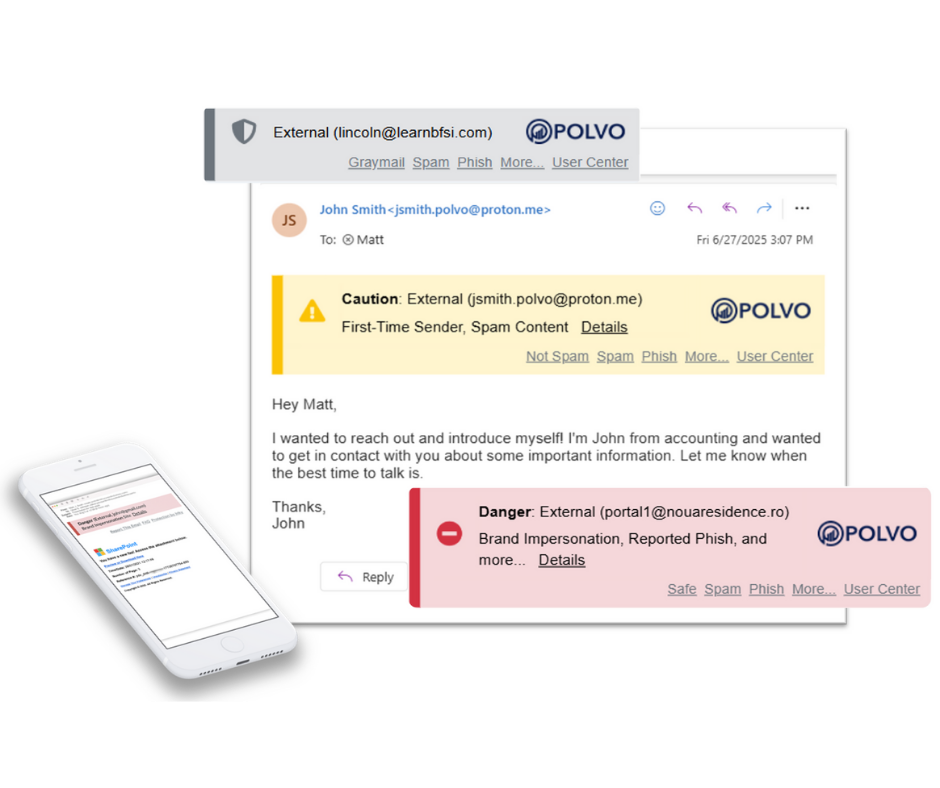
One of the most recognizable—and powerful—features of INKY has always been our banners. Clean, clear, and color-coded, INKY banners turn complex security signals into an intuitive, user-friendly experience. For years, they've empowered users to instantly understand whether an email is safe, suspicious, or dangerous without needing to be a cybersecurity...
Read more
Published on: 07-01-2025

“Looks can be deceiving” is a lesson most of us learn the hard way. It’s the stunning wedding photos that feature bridezilla. Or, taking a big gulp of milk, only to discover it’s spoiled. You get the picture. Unfortunately, far too many companies are learning about malicious QR codes the...
Read more
Published on: 06-18-2025

A Milestone Year for a Growing Threat 2024 marked the 25th anniversary of the FBI’s Internet Crime Complaint Center (IC3) and while their efforts are worthy of celebration, those on the receiving end of cybercrime in 2024 had little to celebrate. The latest annual report paints a sobering picture, as...
Read more
Published on: 05-21-2025
If you’ve ever played Jenga, you’re familiar with just how carefully you must work to build something stable. If you remove the wrong piece or add a new layer too quickly, things can get very wobbly. Building your Managed Service Provider (MSP) business isn’t very different. Every new customer, every...
Read more
Published on: 05-08-2025

Before we get to the article, we could use your input on a new promotion. What if you could earn cash by simply sharing INKY blog posts with your friends and colleagues? Receive a $5 reward for each shared post, payable every time you accumulate $50 in rewards. Sounds easy,...
Read more
Published on: 04-24-2025
Under the current administration, the United States has experienced significant shifts in immigration and deportation policies. In fact, Homeland Security officials said that Immigration and Customs Enforcement (ICE) carried out more than 32,000 arrests in the first 50 days of the new administration.1 The deportation efforts have individuals, families, and...
Read more
Published on: 04-15-2025

Staying informed is the first line of defense when you’re a Managed Service Provider (MSP), protecting your customers from email security threats. To help you stay ahead of that curve, we’re happy to share INKY’s 2024-2025 Email Security Annual Report. Let's dive into some of the key insights that will...
Read more
Published on: 03-25-2025
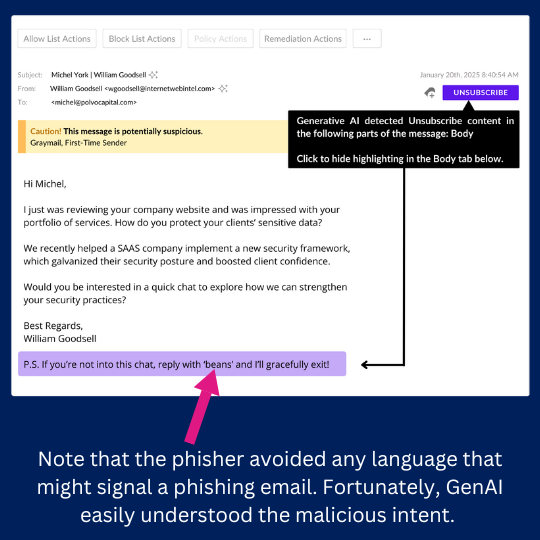
The rapid explosion of Artificial Intelligence (AI) has permeated nearly every industry across the globe. For those of us in email security, AI brings both positive and negative ramifications. When used for good, AI is an incredible tool in the never-ending battle against phishing attacks. However, over on the evil...
Read more
Published on: 01-30-2025

In a significant milestone for global cybersecurity, the United Nations General Assembly has adopted a new, legally binding treaty on cybercrime. This treaty, known as the United Nations Convention against Cybercrime, represents a crucial step in the ongoing battle against digital threats. With cybercrime affecting over two-thirds of the global...
Read more
Published on: 01-09-2025

As a Managed Service Provider (MSP), your days are filled with a myriad of tasks, from monitoring client systems to resolving complex IT issues. But what if you could find more time in your day to take on new customers and expand your business? We’d like to share four tips...
Read more
Published on: 12-05-2024

Cyber Monday sales are expected to hit a record $13.2 billion on Monday, which is 6.1% more than in 2023.1 While this is great for online retailers, it’s important to remember that cybercriminals are just as excited as you are about the holiday rush. ...
Read more
Published on: 12-02-2024
When Telegram CEO, Pavel Durov, was arrested in August of 2024 it put the spotlight on the criminal use of third-party platforms. The arrest came because of what officials believed to be a lack of moderation and cooperation from Telegram in fighting crimes against children. While crimes of this nature...
Read more
Published on: 11-15-2024
Page Visitors

