Resources

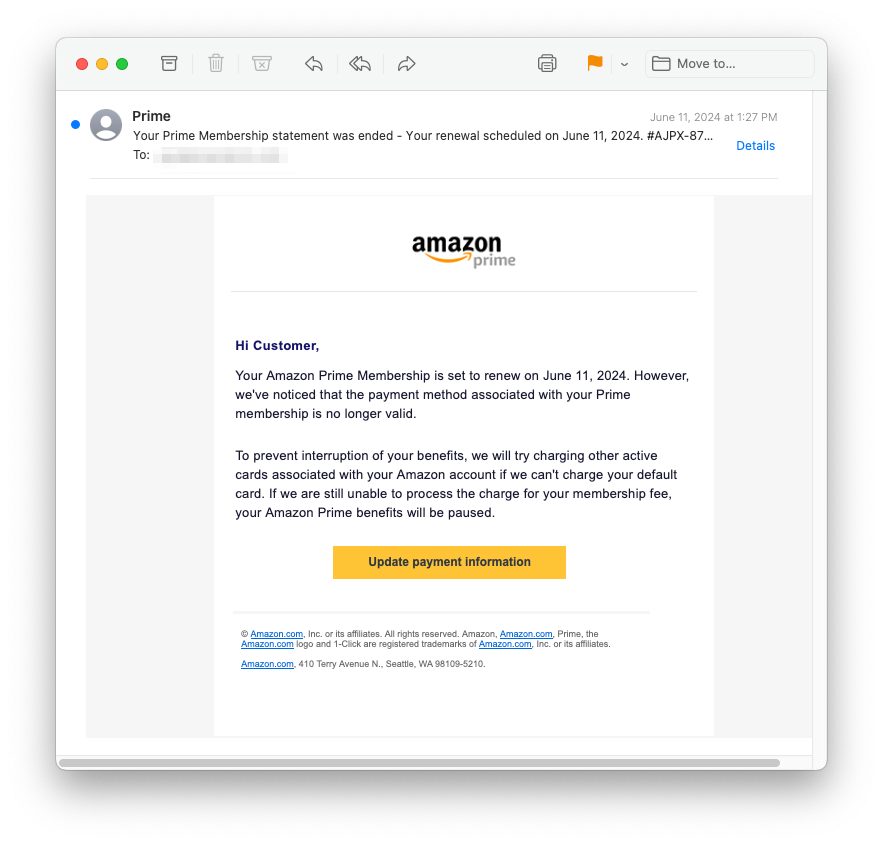
A new phishing scam is leveraging trusted aspects of ecommerce to make their scams look legitimate. ...
Read more
Published on: 07-26-2024

As expected, threat actors are taking advantage of the global IT outage caused by a faulty CrowdStrike update last Friday, SC Media reports. ...
Read more
Published on: 07-26-2024

Declared “dead” by the U.S. Attorney’s Office in 2023, the Russian cyber crime group Fin7 is impersonating some of the top global brands. ...
Read more
Published on: 07-26-2024

Check out the 26 new pieces of training content added in July, alongside the always fresh content update highlights, events and new features. ...
Read more
Published on: 07-26-2024

Check out the July updates in Compliance Plus so you can stay on top of featured compliance training content. ...
Read more
Published on: 07-25-2024
Frequently Asked Questions About KnowBe4's Fake IT Worker Blog July 23, 2024, I wrote a blog post about how KnowBe4 inadvertently hired a skillful North Korean IT worker who used the stolen identity of a US citizen. He participated in several rounds of video interviews and circumvented background check...
Read more
Published on: 07-25-2024
Several threat actors are abusing legitimate cloud services to launch phishing attacks against users in Latin America, according to Google’s latest Threat Horizons Report. ...
Read more
Published on: 07-23-2024

Protecting your financial information has never been more crucial. With the rise of sophisticated scams, it's becoming increasingly difficult to distinguish between legitimate bank communications and fraudulent attempts to access your accounts. So, how can you be sure it's really your bank contacting you? ...
Read more
Published on: 07-23-2024

According to security researchers at Cisco Talos, emails impersonating legitimate officers at the Cyprus Securities and Exchange Commission are being sent to prior Opteck customers that offer victim's with investment advice. ...
Read more
Published on: 07-23-2024
Incident Report Summary: Insider Threat TLDR: KnowBe4 needed a software engineer for our internal IT AI team. We posted the job, received resumes, conducted interviews, performed background checks, verified references, and hired the person. We sent them their Mac workstation, and the moment it was received, it immediately started to...
Read more
Published on: 07-23-2024

Organizations should expect to see phishing attacks exploiting the global IT outage that occurred last Friday, the Business Post reports. ...
Read more
Published on: 07-22-2024

[Security Masterminds Podcast] Securing Software Over 50 Years: Reflections from an Industry Veteran
Does the challenge of keeping up with cybersecurity trends sound familiar? You may have been told to update your antivirus software and hope for the best, only to find that your digital assets are still at risk. ...
Read more
Published on: 07-22-2024

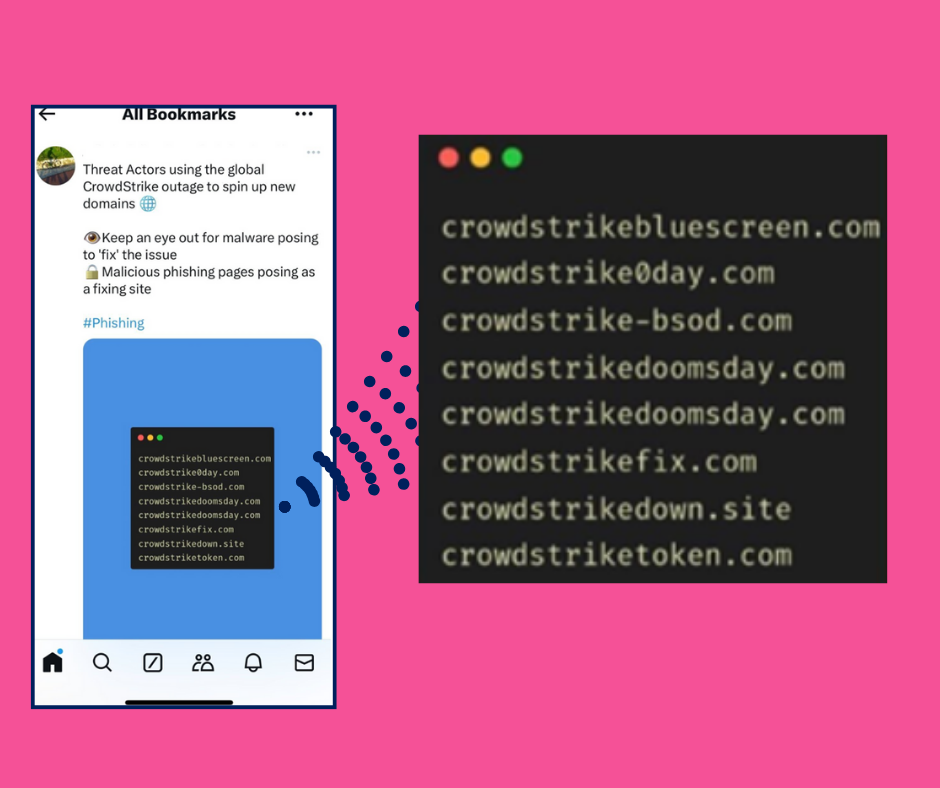
I have been the CEO of an anti-virus software developer. We had a special acronym for catastrophic events like this, a so-called "CEE". As in Company Extinction Event. Within hours of mass IT outages on Friday, a surge of new domains began appearing online, all sharing one common factor: the...
Read more
Published on: 07-19-2024

New data puts the spotlight on the frequency and impact of modern ransomware attacks, highlighting the overconfidence organizations are showing in their ability to defend and respond to attacks. ...
Read more
Published on: 07-19-2024

If you’ve ever bought a raffle ticket, purchased a lottery ticket, or called into a radio station for concert tickets, you’ve pictured yourself on the winning side of a prize. It’s a nice feeling. Whether you chalk it up to serotonin, dopamine, or human nature, winning makes us feel good....
Read more
Published on: 07-25-2024
Millions of companies worldwide are reeling from the major cyber outage caused by a faulty system update released by the cloud-based cybersecurity firm CrowdStrike. Slated by some as causing ‘global chaos’, the outage has impacted hospitals, police stations, airlines, banks, stock exchanges, consumers, and more.1 ...
Read more
Published on: 07-19-2024

In today's digital landscape, email remains a primary target for cybercriminals. Phishing attacks, sophisticated forgeries, and malicious content are constantly evolving, and with language processing tools like ChatGPT, phishers can compose high-quality phishing emails, write code, and create sophisticated malware with minimal effort. It’s a disturbing sign of the times,...
Read more
Published on: 07-12-2024

As a Managed Service Provider (MSP) every client you have counts on you to keep their networks and IT infrastructure up and running, around the clock. It’s not an easy calling and with the current state of cybersecurity, a lot of things could potentially keep you up at night. For...
Read more
Published on: 07-09-2024
The world is gradually learning what INKY and Managed Service Providers (MSPs) have known for some time: Artificial intelligence (AI) is a powerful tool that can be used to improve cybersecurity. ...
Read more
Published on: 05-31-2024
Like any enterprise, there are costs associated with doing business. In the world of cybercrime, threat actors have plenty of options. ...
Read more
Published on: 05-23-2024
The 2024 FBI Internet Crime Report has revealed some frightening new trends and statistics that should have every business pausing to consider the state of their organization’s email security. Losses due to cybercrime have reached an all-time high of $12.5 billion, up 21.4% from the prior year.1 And, as predicted,...
Read more
Published on: 05-09-2024
There are not a lot of email security platforms that can detect a phish hiding behind a Rich Text Format (RTF) attachment file. However, that’s exactly what was caught in a new phishing scam that took a very personalized approach to harvesting Microsoft credentials. With multiple versions at play, it’s...
Read more
Published on: 04-30-2024

There is a lot of talk about vendor consolidation these days, and with good reason. When it comes to email security, the more vendors your customers have, the greater their risk. ...
Read more
Published on: 04-12-2024
Phishing threats continue to be the most frequently used form of cybercrime, accounting for 34% of all complaints received by the FBI’s Internet Crime Complaint Center (IC3).1 This means costly trouble for individuals and businesses alike. For those wondering how phishing maintains its top position each year, the most obvious...
Read more
Published on: 04-04-2024
Looking for the tell-tale signs of a phishing email is something many of us have come to do automatically. However, things get much trickier when the phishing emails come in the form of legitimate Adobe notifications, have been authenticated (SPF & DMARC) by adobe[.]com, and use actual Constant Contact tools...
Read more
Published on: 03-12-2024
The State of Email Security If there is one thing about email security and phishing that you can count on, it’s cybercrime’s consistent upward climb. Year after year, phishers are improving their skills - devising more complicated phishing threats, designed to slip by Secure Email Gateways (SEGs) and fool recipients....
Read more
Published on: 02-20-2024

Whether it’s your favorite streaming service, or the laundry detergent that smells like your childhood, we all have our go-to brands. Why? Because the brands we love stand for something. They make our life better. They have value. They’re also familiar – we can recognize their logo instantly. ...
Read more
Published on: 01-19-2024

We all have one, so call it what you will. Your John Hancock, autograph, inscription, endorsement, seal, scrawl, or our favorite…your ink(y). It’s more than just a few lines on a paper. Whether it’s the curve of your letters or the middle name that’s carried through your family for decades,...
Read more
Published on: 11-09-2023
Page Visitors