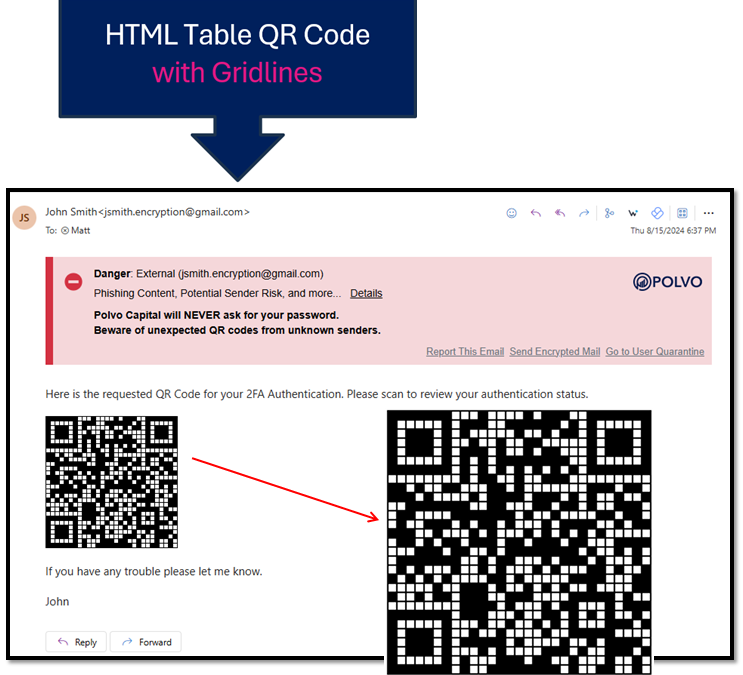
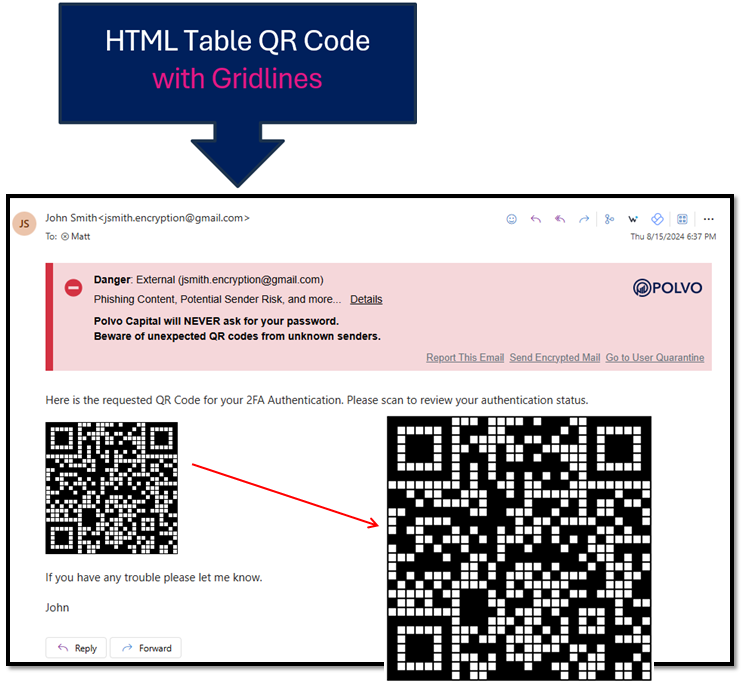
QR code phishing has become one of the most rapidly growing forms of phishing, especially since QR codes gained popularity during the global pandemic. Recently, INKY has observed a new evolution of this tactic, where QR codes are constructed using HTML tables and ASCII characters. We’ve noticed this technique emerging over the past few months and have implemented protections against it. Now, we’d like to share how it works and how we defend against it.
![]()

Recent Comments